Unleash your possibilities
Fuel your growth and transformation — with an integrated payments partner that’s as passionate about you, as you are about your customers.
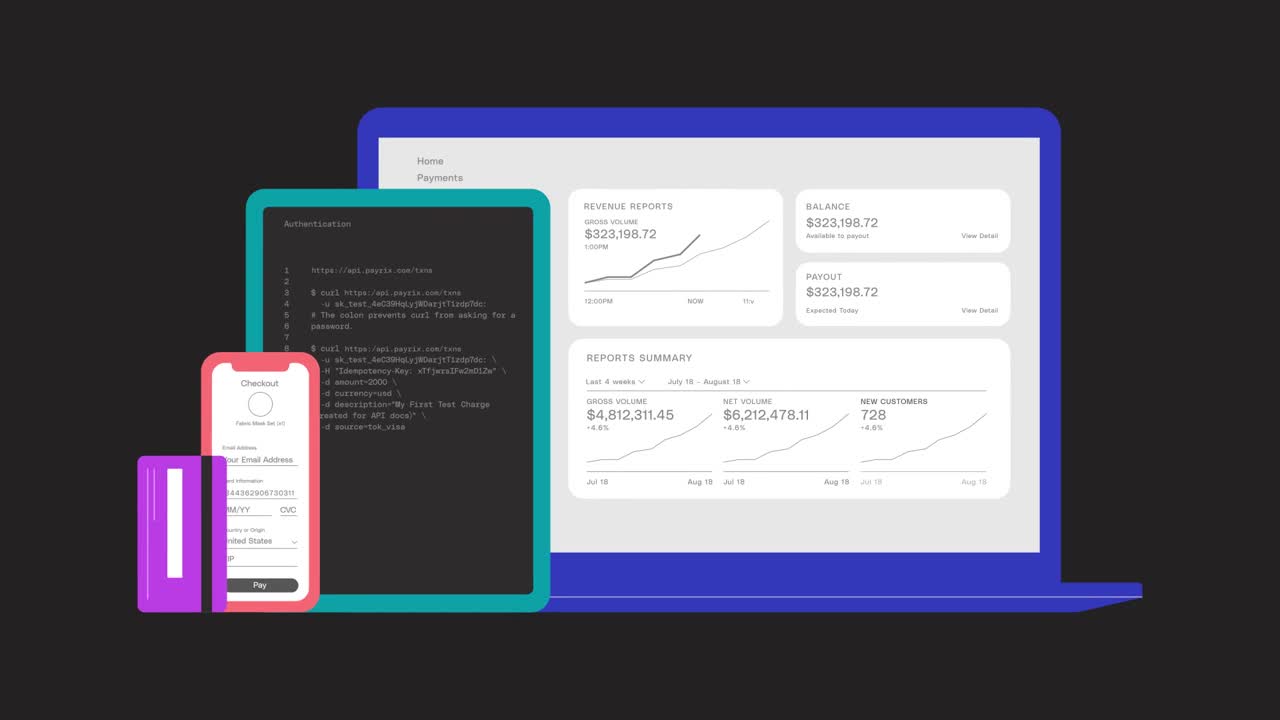
Powered by Payrix









How Payrix works
The only integrated payments partner you need
UNLOCK YOUR REVENUE POTENTIAL
See what you can earn by monetising payments
With Payrix, you can create a new revenue stream by monetizing payments processed through your platform. Our free ROI calculator allows you to estimate the potential earnings for your business. Start generating profits from every transaction today.
Calculate your ROIPayments that are just your type
Whether you prefer recurring, one-off, real-time, online, in-person or invoicing, Payrix supports all your payment needs with an all-in-one platform.


Get real-world guidance from payments experts
Navigating payments and compliance can be challenging. Allow our team of expert payments and software professionals to guide you with no-pressure advice. Contact us today to learn more.
Contact Us
DOWNLOAD FREE EBOOK
SaaS Payments 101
Unlock the potential for increased revenue per customer with our complimentary in-depth eBook. Discover proven strategies for scaling your business through payments and learn how to develop a pricing plan that maximizes ROI and generates up to 2-5x more revenue per customer. Get your free copy now.
Download Now
Experience uncapped possibilities
Maximize your freedom and flexibility with Payrix’s fully integrated solution, which reduces interruptions and obstacles and helps you power your potential through:
- Advanced, industry-leading payment capabilities
- Fully customizable, collaborative options
- Premium, hands-on support
- Built-in fraud and data protection
- Compliance with PCI and AFSL standards
- Strong technical infrastructure
- Opportunities to increase business revenue
With Payrix, you can experience the benefits of payments without the complexity.
Chat to us todayWe get payments
RESOURCE CENTRE
Browse our Documentation
Looking for something? Try our handy resource centre for in-depth information and guidance on integrating with Payrix, maximising your solution, and getting the most out of your powerful payment features.
Go to Resource Centre